Making Diamond work for your team
While Diamond will catch bugs out of the box, you can customize its behavior to better match your team’s specific needs and coding standards. Diamond offers two primary customization options: Exclusions and Custom rules.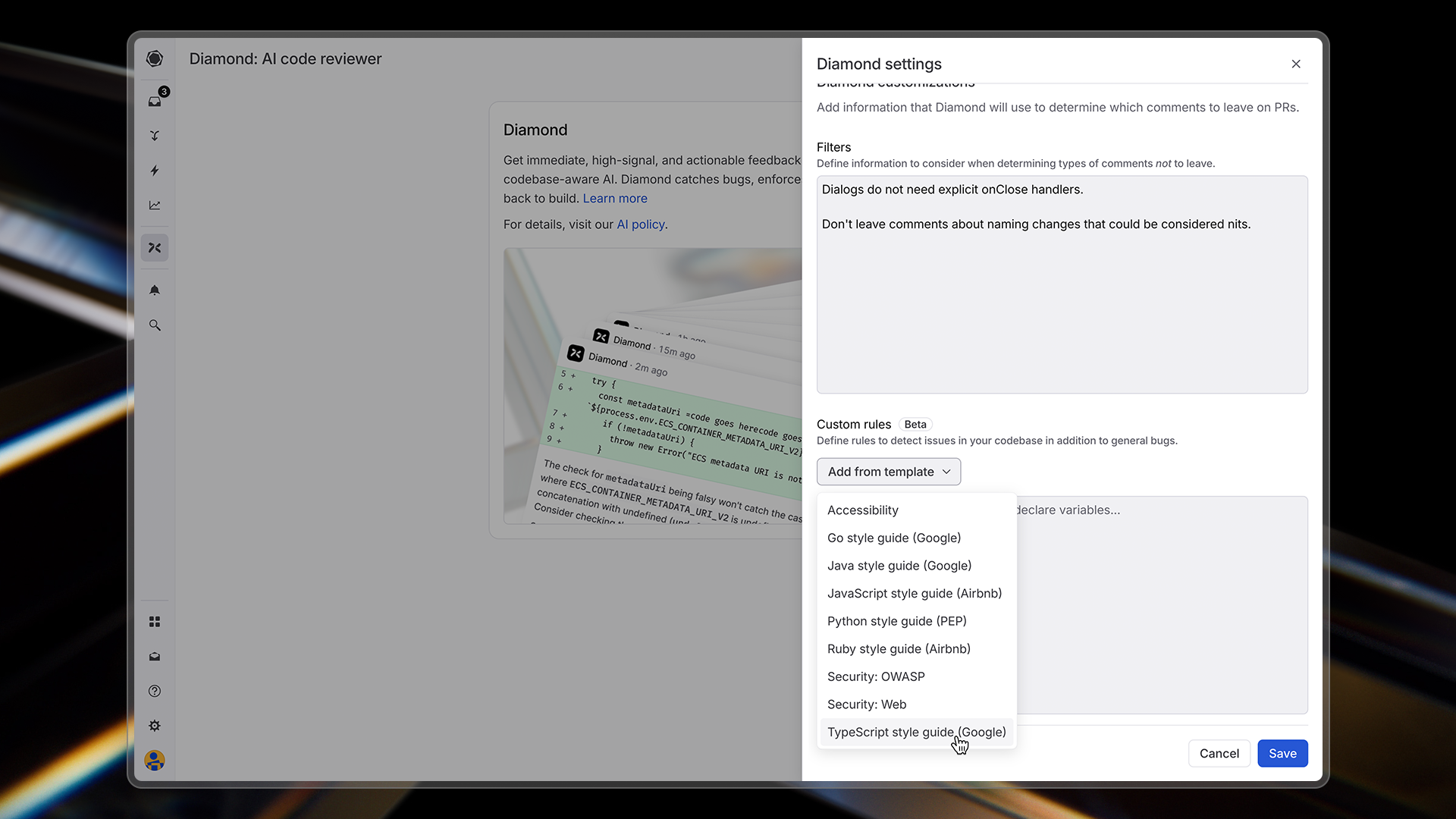
Diamond's customization interface
Exclusions: Specifying what Diamond should ignore
Comment exclusions allow you to specify situations where Diamond should not leave comments. This reduces noise and places Diamond’s focus on what matters most to your team. Common exclusion use cases:- Ignore generated code: Prevent extraneous comments on generated code from build artifacts, schemas, and other generated files.
- Skip specific types of comments: Turn off categories of feedback that aren’t relevant to your team
- Ignore certain repositories or directories: Focus Diamond’s attention where it matters most
- Exclude specific patterns: Define patterns that Diamond should not flag (e.g., team-specific style conventions)
Best practices for writing exclusions
Make the language as targeted as possible by specifying the exact scope where the exclusion should apply. If an exclusion is written too broadly, then Diamond may not leave valid comments. Bad example:- This is too broad and would miss legitimate performance issues. The rule could be rewritten instead as:
- Go to the Diamond settings page
- Click on Workspace Settings
- Create and save your exclusions
Custom rules: Teaching Diamond your standards
Custom rules allow you to define explicit guidelines for Diamond to follow when reviewing your code. This is especially powerful for enforcing team-specific best practices. With custom rules, you can:- Define coding standards specific to your codebase
- Implement architectural guidelines for your team
- Enforce security or performance best practices
- Ensure consistent patterns across your repositories
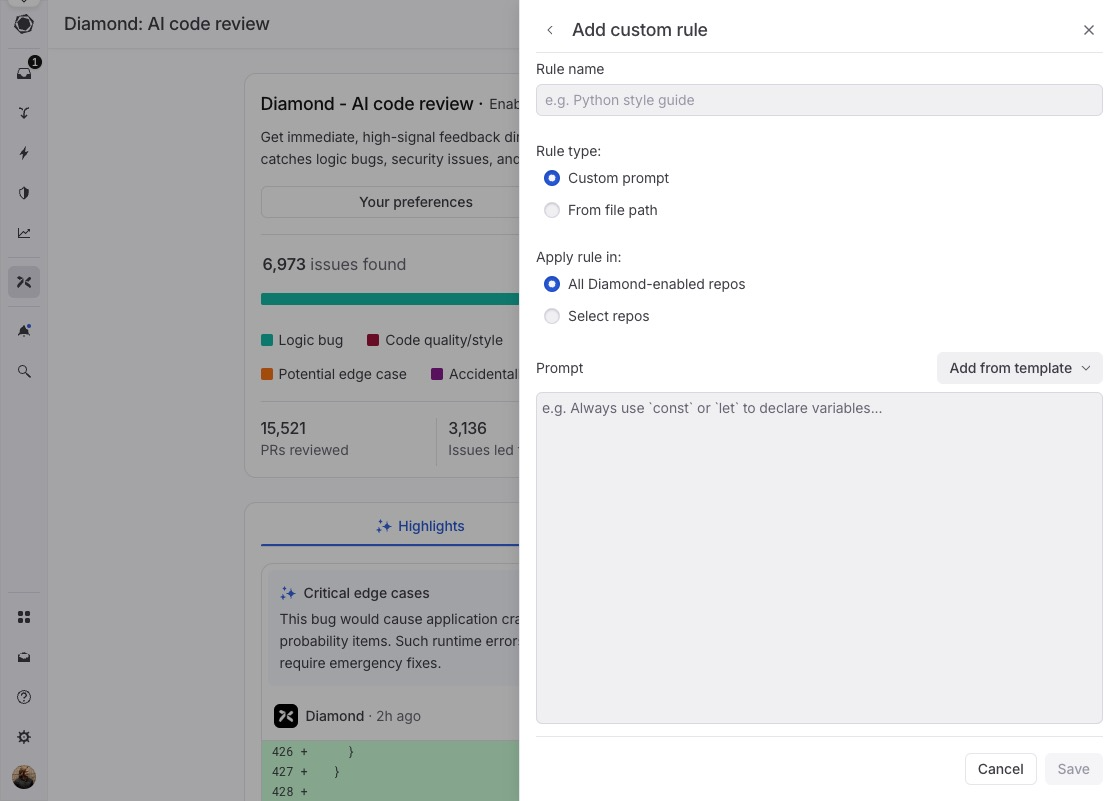
Diamond's custom rule interface
Custom prompts (Recommended)
Custom prompts are rules written directly in the Graphite UI. They’re the recommended approach for most teams. Why custom prompts work best:- Focused: Each rule addresses one specific concern
- Fast to iterate: Test and refine rules based on their effectiveness
- Better performance: No file processing overhead
- Easy to manage: All rules across all repos visible in a single interface
-
Use Diamond’s built-in templates for common scenarios:
- Language-specific style guides (JavaScript, Python, Go, etc.)
- Security best practices
- Accessibility standards
-
Start small: Create focused rules that address specific concerns
- Example: “JavaScript error handling patterns”
- Example: “API response formatting standards”
- Quick start: Copy relevant sections from your existing coding guidelines and refine them into focused rules
File-based rules
File-based rules reference existing documentation in your repository using glob patterns. Use these sparingly when you have living documentation that changes frequently. When to use file-based rules:- Documentation maintained by other teams that changes regularly
- Shared architectural decision records across repositories
- Style guides that are actively updated
- Specify a glob pattern (e.g.,
docs/coding-style.md) - Diamond reads the file content from your repository
- Uses that content as context during code review
- Large files are truncated for performance
- Too many files can reduce review quality
- Glob patterns are case-sensitive
Best practices for writing custom rules
Structure your rules clearly:- Format: Rule → Bad example → Good example → Reasoning
- Focus: One specific concern per rule
- Examples: Provide 2-3 clear, contrasting examples
- Test: Try your rule on recent PRs to verify it adds value
- Language-specific conventions (naming, imports, error handling)
- Security guidelines (authentication, data validation)
- Framework-specific patterns (React hooks, API design)
- Overly broad rules (“write good code”)
- Subjective preferences without clear reasoning
- Complex architectural patterns that only sometimes apply
- Too vague. The rule needs to specify what types of field drops or additions would be considered breaking.
- Not actionable. The rule should be specific, like: “Never drop a required field directly. Always make it nullable first and stop writing to it so that it is no longer used by the entity.”
- No examples provided.
- More context is needed. The rule should specify which files or frameworks this applies to (CSS files, styled-components, etc.).
- This isn’t phrased as a rule. The rule should be stated clearly as “Never use hex color values directly, always use design system tokens instead.”
- This prompt mixes custom rules and exclusions. The latter sentence is not necessary.
- Go to the Diamond settings page
- Scroll to the “Custom rules” section and click on “Create custom rule”
- Choose a template or add a custom prompt for your new rule
- Save your configuration
Excluding files from Diamond review
For large repositories, you may want to exclude certain files from Diamond’s analysis. This is useful for:- Data files that don’t need to be reviewed
- Generated code that is automatically created by tools
- Any files that would make a PR too big for Diamond to analyze
.gitattributes file:
linguist-generated will be:
- Automatically collapsed in GitHub pull request views
- Excluded from Diamond’s analysis when determining if a PR is too large
- Skipped during Diamond’s code review process
PR-level filtering for Enterprise organizations
Enterprise organizations have access to advanced PR-level filtering capabilities that provide granular control over when Diamond runs code reviews. This Enterprise-only feature allows you to configure Diamond to only analyze certain pull requests based on specific criteria. With PR-level filtering, you can control Diamond based on:- PR author: Run Diamond only for specific team members or external contributors
- File paths: Analyze PRs only when certain files or directories are modified
- PR labels: Trigger Diamond based on GitHub labels applied to pull requests
- PR title and description: Filter based on text content in PR titles or descriptions
- Parent branch: Run analysis based on target branch naming conventions
- Control usage and costs: Optimize Diamond usage by focusing on the most important PRs
- Focus analysis on critical PRs: Ensure Diamond reviews high-impact changes while skipping routine updates
- Implement organization-specific review policies: Align Diamond’s behavior with your team’s development workflows and governance requirements

